TL;DR
- For a simple MVP (e.g., a basic sensor reporting data), budget $50,000–$80,000 over 3–4 months. For a more complex system (custom firmware, edge processing), plan for $150,000–$250,000+ over 6–9 months.
- Always start with a pilot. Test your entire system—hardware, connectivity, and cloud—end-to-end with a small user group before scaling. This de-risks the project and exposes flaws early.
- Adopt a security-first mindset. Your biggest risk is the physical device. Use unique credentials for every device, encrypt data in transit and at rest, and implement a secure Over-the-Air (OTA) update process.
- Hire specialized roles. IoT requires a mix of embedded systems, cloud, and data engineers. A general software team will struggle with the unique constraints of hardware and firmware development.
Who this is for
- CTOs & Heads of Engineering: Deciding on architecture, team composition, and budget for a new IoT initiative.
- Founders & Product Leads: Scoping an IoT MVP and understanding the time-to-value and key risks.
- Talent Ops & Procurement: Evaluating the specific skills needed to build a successful IoT team.
This guide provides a step-by-step framework for planning, building, and scaling an IoT application, with practical examples and checklists you can use today.
Your IoT Application Development Framework
Before a single line of code is written, you need a clear plan. Building a successful Internet of Things (IoT) solution is about orchestrating an entire ecosystem to solve a specific business problem.
Are you predicting machine failures to cut downtime, or building a smart asset tracking system to streamline logistics? This initial clarity guides every decision and directly impacts your budget, timeline, and final product capabilities.
Key Development Phases
A typical IoT project moves through five distinct phases.
- Strategy and Scoping: Define user needs, business objectives, and the key performance indicators (KPIs) that measure success.
- Hardware Selection: Choose sensors, gateways, and devices, carefully weighing power consumption, operating environment, and cost.
- Platform and Architecture: Decide whether to build a custom backend or use a managed IoT platform. This choice has massive implications for your time-to-market.
- Security by Design: Build security in from the ground up, implementing end-to-end data encryption, secure boot, and strict access controls.
- Scaling and Management: Plan how you'll onboard new devices, push remote firmware updates (OTA), and manage data as your network grows.
To see how these phases come together, this guide on IoT in property management offers practical context. Your early architectural decisions are critical. One of the biggest is whether to build a custom solution or use a platform.
Decision Matrix: Custom Build vs. IoT Platform
Bottom Line: A custom build offers unparalleled control for highly specialized applications. However, an IoT platform like AWS IoT or Azure IoT Hub dramatically accelerates development, making it the best choice for most teams aiming for a fast and reliable market launch.
The 4 Core Components of an IoT Ecosystem
An IoT ecosystem is like a nervous system: sensors feel the world, networks transmit signals, a cloud platform processes the information, and an application turns that data into action.
Mastering the interplay between these four layers is a practical blueprint for success. Neglecting one layer introduces security holes, scaling issues, or a poor user experience.
The Device and Sensor Layer
This is where your solution physically touches the world. This layer includes the sensors, actuators, and embedded systems that collect data or perform commands.
- Sensors gather data (temperature, motion, light).
- Actuators perform physical tasks (flip a switch, turn a valve).
- Embedded Systems are the microcontrollers (MCUs) or microprocessors (MPUs) that provide device intelligence.
The key trade-off here is between power consumption, processing capability, and cost. A smart home sensor can use a low-power MCU, while an industrial camera using AI for defect detection needs a powerful processor.
The Connectivity and Network Layer
This layer is the highway that moves data from devices to the cloud. Choosing the right communication protocol is critical and involves trade-offs in range, bandwidth, and power usage.
Common options include:
- Wi-Fi: High bandwidth, short-range, for powered devices.
- Bluetooth Low Energy (BLE): Low power, short-range, for devices like fitness trackers.
- Cellular (4G/5G/NB-IoT): Wide-area coverage for mobile assets.
- LoRaWAN: Long-range, low-power transmission for small data packets (e.g., smart agriculture).
For messaging, MQTT (Message Queuing Telemetry Transport) is the lightweight workhorse, while CoAP (Constrained Application Protocol) is designed for resource-constrained devices.
The Data Processing and Cloud Layer
This is the central brain of your operation, where raw data becomes valuable insight. Cloud platforms like AWS IoT, Azure IoT Hub, or Google Cloud IoT are essential here.
Massive data streams are ingested, stored in specialized time-series databases, and fed into analytics engines. This is where you turn sensor pings into business intelligence, like identifying which factory machine is likely to fail next week.
The market for this is exploding. The value of IoT applications was around $595.73 billion in 2023 and is on track to hit a staggering $4,062.34 billion by 2032. You can read more about these IoT application trends to see where things are headed.
The Application Layer
This is the part of the system users see and interact with—your web dashboard, mobile app, or API. This is where business value is realized.
A great application layer makes complex data simple and actionable, whether it's a dashboard showing factory efficiency or a mobile app letting a homeowner adjust their thermostat.
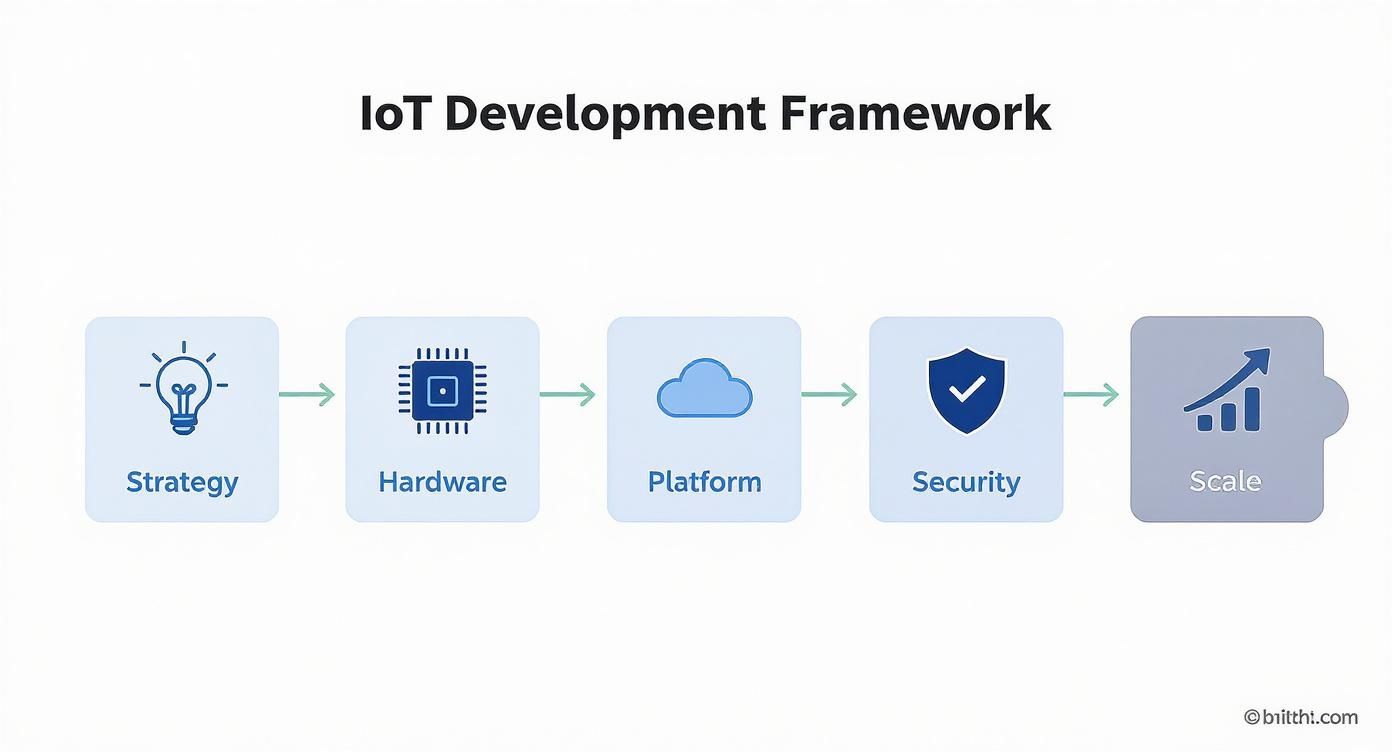
alt text: Infographic showing the five key stages of an IoT application development framework: Strategy, Hardware, Platform, Security, and Scale, arranged in a horizontal flow.
This visual clarifies that security is not a step but a foundational layer woven through the entire lifecycle.
Practical IoT Application Architectures
A solid architecture is the difference between a system that works and one that is cost-effective, secure, and scalable. Let's examine two practical examples for different use cases.
Example 1: Lean Architecture for Smart Home Monitoring
Goal: Build a cost-effective smart home security system with low device costs, minimal operational expenses, and reliable notifications.
A lean, serverless architecture is the ideal choice.
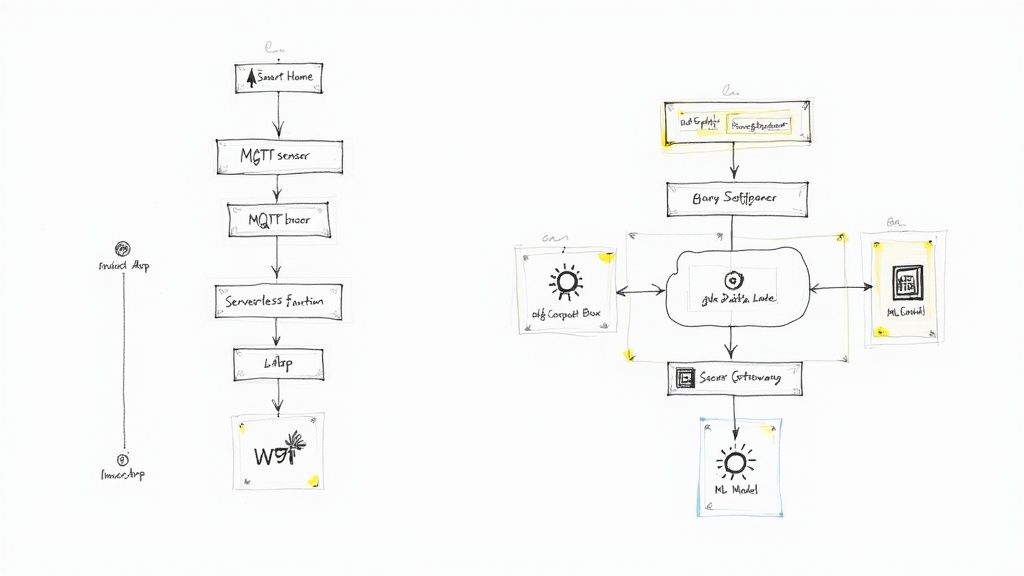
alt text: Annotated diagram showing a lean architecture for a smart home system. It illustrates data flowing from low-power sensors via MQTT to a cloud broker, triggering serverless functions for processing and sending push notifications to a mobile app.
Here’s the data flow:
- Low-Power Devices: Battery-powered sensors use MQTT over Wi-Fi to send tiny data packets (e.g., "door open"). This design ensures long battery life.
- MQTT Broker: A cloud-based broker like AWS IoT Core acts as a traffic controller, authenticating devices and routing messages.
- Serverless Functions: AWS Lambda or Google Cloud Functions spin up only when a message arrives, executing simple logic.
- Processing Logic: The function checks the system's state (e.g., "armed") and crafts a push notification if needed. This is highly cost-effective, as you only pay for milliseconds of compute time. To learn more, see our guide on how to reduce software development costs.
- Notification Service: The function passes the alert to a service like Apple Push Notification Service, which delivers it to the user's phone.
This event-driven architecture is perfect for applications with sporadic activity, enabling you to support thousands of users at a very low cost.
Example 2: Robust Architecture for Industrial Predictive Maintenance
Goal: Monitor factory machinery to predict failures, requiring extreme reliability, data integrity, and low-latency alerts.
This industrial IoT (IIoT) use case demands a robust architecture with edge computing.
Key Concept: Edge Computing
Edge computing processes data locally on-site, near the device. Instead of sending all raw data to the cloud, you analyze it at the "edge" of the network. This reduces latency, saves bandwidth, and allows the system to operate even if the cloud connection is lost.
The architecture is more complex:
- Industrial Sensors & PLC: Vibration sensors and thermal cameras are wired into a Programmable Logic Controller (PLC), collecting hundreds of readings per second.
- IoT Edge Gateway: A rugged, on-site computer runs analytics models in real-time, filtering the data stream for anomalies that signal impending failure.
- Secure Ingestion: The gateway aggregates, filters, and encrypts data before sending only important events or summaries to the cloud. This dramatically reduces bandwidth and storage costs.
- Cloud Data Lake & ML Pipeline: Processed data is stored in a scalable data lake (e.g., Amazon S3). From there, it feeds a machine learning pipeline to train predictive models. Effective data management relies on building robust data pipelines.
- Dashboards & Alerts: Refined models are pushed back to the edge gateways. Critical alerts are sent to a dashboard for plant managers, enabling proactive maintenance.
This hybrid edge-cloud approach provides the immediate response of local processing with the analytical power of the cloud.
Key Challenges in IoT Development
Even with a solid architecture, IoT application development presents unique hurdles. You must address security, scalability, and data management from day one.
Fortifying the Ecosystem Against Threats
In IoT, security is non-negotiable. Every connected device is a potential entry point for an attacker. The only viable strategy is a defense-in-depth approach that secures both the device and the network.
A Security-First Design Checklist
This is a non-negotiable starting point for any project:
- Secure Boot: Ensure devices only run authenticated firmware.
- Data Encryption: Encrypt data at rest (on the device) and in transit (across the network).
- Unique Credentials: Eliminate default passwords. Every device needs a unique identity.
- Firmware Signing: Cryptographically sign all Over-the-Air (OTA) updates to prevent malicious code injection.
- Limited Attack Surface: Disable unused ports and services.
Ignoring security is a recipe for operational disaster and reputational damage.
Preparing for Growth and Scalability
An IoT system that works for 100 devices may fail at 10,000. Scalability must be designed into your backend architecture. A critical early decision is choosing between a monolithic or microservices architecture.
- Monolithic Architecture: A single, unified application. Simpler to build and deploy initially, making it a good choice for MVPs or small pilot projects where speed is critical.
- Microservices Architecture: The backend is broken into small, independent services. More complex to set up but offers superior scalability and resilience, as a failure in one service doesn't bring down the entire system.
Our recommendation: Start with a monolith to validate your idea quickly. If you anticipate rapid growth and need the agility to scale components independently, plan your migration to microservices. Complex microservices projects often require specialized skills, which is where IT outsourcing for development can provide crucial expertise.
Taming the Data Deluge
IoT devices produce a relentless stream of time-series data. Relational databases are not built for this high-speed ingestion and will quickly become a bottleneck.
This has led to the rise of specialized databases. Your choice here directly impacts system performance and analytical capabilities. Two main contenders emerge: NoSQL databases and dedicated Time-Series Databases (TSDBs).
For most IoT applications that analyze sensor data over time, a purpose-built TSDB like InfluxDB is the clear winner. It is optimized for the exact data patterns you'll encounter, ensuring faster queries and a more efficient system.
How to Build Your IoT Development Team
Building an IoT product requires a unique blend of hardware, firmware, cloud, and data expertise. A general software team will struggle.
Successful IoT application development requires a team that understands the entire system, from the microcontroller code to the user-facing dashboard.
Core Engineering Roles
A strong IoT team is built on four technical pillars. A weakness in any one area creates a project-wide bottleneck.
- Embedded Systems Engineers: Write low-level code for the device, managing hardware, battery life, and communication.
- Cloud and Backend Engineers: Build the scalable cloud services that ingest, process, and serve data via APIs.
- Data Engineers: Architect the data pipelines that channel, clean, and organize the massive influx of information for analytics.
- IoT Security Specialists: Protect every link in the chain, from device authentication to data encryption and threat monitoring.
These are specialized roles. For more on how they fit into the broader tech landscape, see our guide on jobs in software engineering.
Essential Roles and Skills for Your IoT Project Team
Use this table to define roles and screen candidates effectively. A common mistake is hiring a brilliant backend developer and expecting them to handle the unique constraints of embedded firmware.
Having people with these specific skills is the most important step toward building a reliable, secure, and scalable IoT solution.
Your IoT Project Launch Checklist
This checklist breaks down the IoT application development lifecycle into actionable phases. Use it to de-risk your project and ensure no critical steps are missed.
alt text: An engineer works on a circuit board, representing the hands-on nature of IoT development and project planning.
Phase 1: Pre-Project Scoping (Weeks 1–4)
This foundational phase is about achieving alignment to prevent scope creep and budget overruns later.
- Define business objectives and KPIs: What specific, measurable outcome will define success?
- Identify user personas and core use cases: Who are you building this for? What problem does it solve?
- Conduct a hardware feasibility study: Evaluate sensor accuracy, power consumption, and environmental durability.
- Choose a connectivity strategy: Justify your choice of Wi-Fi, Cellular, LoRaWAN, etc., based on range, bandwidth, and cost.
- Draft a preliminary data management plan: Where will data live, who owns it, and how will you ensure privacy and compliance?
Phase 2: Development and Testing (Months 2–6)
This phase is an iterative loop of building, testing, and refining the entire system, not just individual components.
A classic mistake is testing in isolation. Firmware may work on the bench and an API may pass unit tests, but they must perform together under real-world network conditions.
- Develop and test device firmware: Optimize code for low-power, memory-constrained devices.
- Build and deploy cloud infrastructure: Set up data ingestion pipelines, databases, and application logic.
- Conduct end-to-end integration testing: Verify secure data flow from the device to the end-user application.
- Perform a comprehensive device security audit: Include penetration testing and vulnerability scanning.
- Run a pilot program with a small user group: Collect feedback on performance, usability, and reliability.
Phase 3: Deployment and Maintenance (Ongoing)
Launching the product is just the beginning. This phase focuses on scaling the solution and ensuring its long-term health.
- Finalize the device manufacturing and provisioning process: Define a secure method for onboarding new devices at scale.
- Establish a device lifecycle management protocol: Plan for device activation, deactivation, and end-of-life.
- Implement a monitoring and alerting system: Track device health, connectivity, and application performance in real-time.
- Plan for over-the-air (OTA) firmware updates: Implement a secure and reliable way to push updates to devices in the field.
What To Do Next
- Scope Your Pilot: Use the Phase 1 checklist to define the core features, hardware, and KPIs for your minimum viable product.
- Define Your Team: Based on the roles table, identify the key hires or contractors you need to execute the pilot.
- Book a Scoping Call: Get expert help to validate your architecture and plan your team.
Ready to build your IoT solution with a team of vetted experts? ThirstySprout connects you with top-tier embedded systems, cloud, and data engineers who can accelerate your project from concept to scale. Start a Pilot and deploy your IoT team in weeks, not months.
Hire from the Top 1% Talent Network
Ready to accelerate your hiring or scale your company with our top-tier technical talent? Let's chat.

