TL;DR: Your Security Hiring Framework
- Define Roles by Business Risk: Don’t hire for a generic title like "Security Analyst." Hire for a specific mission, like "Secure our AWS environment to pass our SOC 2 audit." This clarifies the role's value and attracts mission-driven candidates.
- Use Realistic, Hands-On Assessments: Ditch trivia. Use practical take-home challenges (2–3 hours max) or live threat-hunting simulations that mirror real-world tasks. This tests problem-solving ability, not just memorization.
- Source Where Talent Lives: Top security pros aren't scrolling job boards. Engage them on GitHub, niche Discord/Slack communities, or after a conference talk. Personalized, problem-focused outreach is non-negotiable.
- Move with Urgency: A slow hiring process is a security liability. Aim to complete the entire cycle, from first contact to signed offer, within 2–4 weeks. Anything longer and you will lose top candidates to faster competitors.
- Onboard for Impact: A structured 90-day plan is your best retention tool. Focus the first 30 days on immersion, the next 30 on contribution, and the final 30 on proactive impact.
Who this guide is for
This guide is for you if you're a:
- CTO, Head of Engineering, or Staff Engineer under pressure to fill critical security roles and reduce organizational risk.
- Founder or Product Lead trying to scope security roles and budget for a secure product launch or compliance milestone.
- Talent or Operations Leader tasked with finding, vetting, and hiring specialized security talent in a highly competitive market.
You need to hire the right security expert within weeks, not months, and ensure they deliver immediate business value.
The 3-Phase Framework for Security Recruitment
Building a top-tier security team is about executing a deliberate plan to reduce business risk. For any leader under pressure to staff up, success isn’t luck. It comes from a repeatable process focused on three core phases: defining the mission, assessing real-world skills, and making your company an irresistible destination for top talent.
For a broader look at creating a repeatable system for attracting talent, review this a guide to building a winning talent strategy.
The visualization below outlines the essential pillars of an effective hiring plan.
Alt text: A flowchart showing the three pillars of information security recruitment: Define the role, assess skills, and attract talent.
This shows the importance of a structured flow. You start with a precise role definition based on business risk, move into a rigorous, hands-on assessment, and finish with attraction tactics that resonate with security professionals.
The Stark Reality of the Security Talent Market
The market for security professionals is incredibly competitive. Recent data from the ISACA report on the state of cybersecurity shows that 65% of organizations have open cybersecurity positions, and 55% admit their teams are understaffed.
This talent crunch directly impacts hiring velocity. A staggering 38% of organizations report it takes three to six months to fill even an entry-level security role. That's a long time to leave a critical gap in your defenses.
A slow hiring process is a security liability. Every week a critical security role remains unfilled is another week your organization operates with a known vulnerability in its human defenses. The goal is to move with speed and precision.
Connecting Recruitment to Business Impact
An effective recruitment strategy is a core part of your risk management program. Every security hire must map directly to a business need, whether that’s protecting customer data, achieving SOC 2 compliance, or securing a new cloud environment.
- Reduced Breach Risk: The right Cloud Security Engineer finds and fixes vulnerabilities before they are exploited, preventing a costly data breach.
- Increased Customer Trust: A sharp Governance, Risk, and Compliance (GRC) analyst ensures you meet industry standards, which is fundamental to winning and retaining enterprise customers.
- Faster, Secure Innovation: A DevSecOps professional bakes security into your development lifecycle, allowing engineering teams to ship features faster and more securely.
Framing your hiring needs in these terms clarifies the role’s importance and builds a stronger business case for the investment. If you need to accelerate this process, specialized tech talent hiring solutions can connect you with pre-vetted experts.
Practical Example 1: Crafting an Outcome-Driven Job Description
A generic job description attracts generic candidates. To win top security talent, you must move past vague titles and craft a compelling narrative that connects real business problems to the specific skills you need.
It’s about showing a candidate exactly how their work will reduce risk.
Alt text: A security leader writing a clear, outcome-driven job description on a laptop.
This shift ensures you’re hiring a problem-solver. It’s the difference between hiring someone to "manage firewalls" and hiring someone to "defend our core revenue-generating applications from determined attackers." One is a task; the other is a mission.
Don't hire for a title; hire for a mission. A great job description sells a candidate on the problem they get to solve. It makes the role feel meaningful from the very first read.
This business-first mindset prevents you from creating a "purple squirrel" job description—that mythical candidate who has mastered every tool. It forces focus on what truly matters. Knowing why AI-friendly job descriptions matter is another key to getting your role seen.
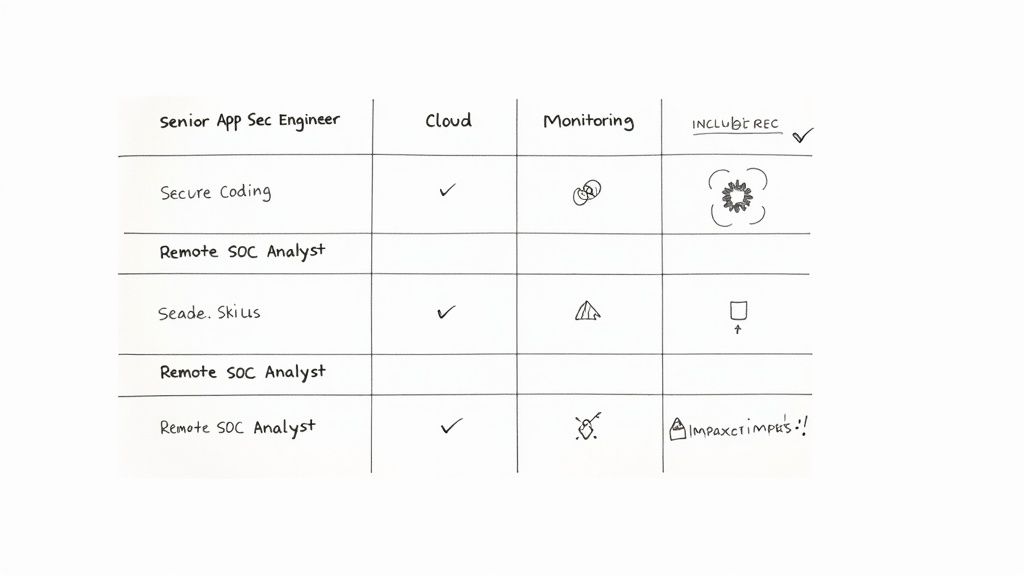
Skills Matrix for a Senior AppSec Engineer
A skills matrix is more effective than a bulleted list. It brings clarity for both you and the candidate, showing what's truly important versus what can be learned.
This matrix immediately signals that strong collaboration and hands-on code review skills are more critical than just operating a specific tool.
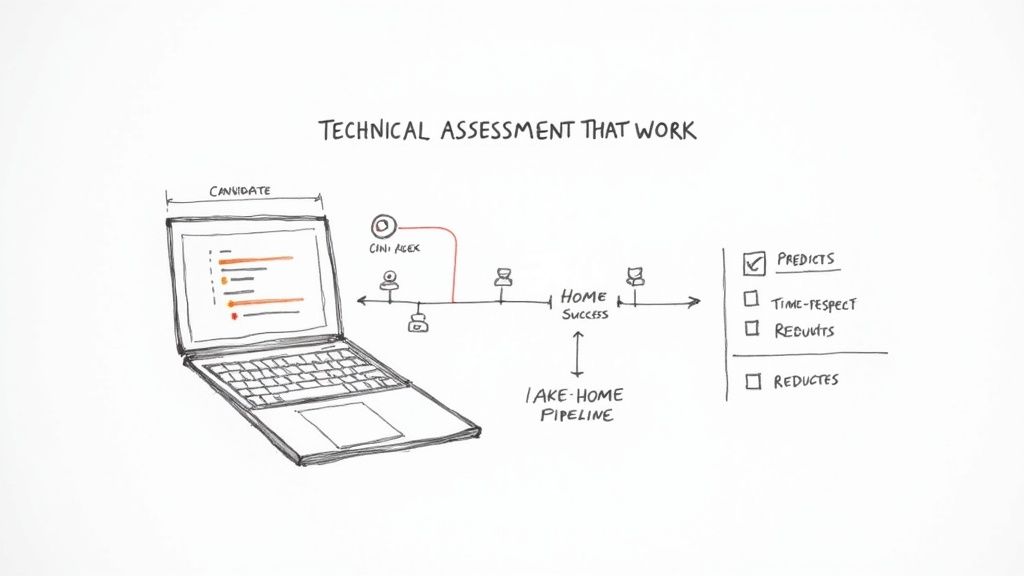
Practical Example 2: A Realistic Technical Assessment
The technical assessment is often the most broken part of security hiring. Too many companies use brain teasers or trivia that have little to do with the actual job. They test memorization, not a candidate's ability to solve problems.
A great technical assessment feels less like an exam and more like a collaborative work session.
The DevSecOps Take-Home Challenge
A take-home project works well for roles like DevSecOps, where work is often focused and asynchronous. It must be meaningful but respectful of the candidate’s time.
The Scenario: "We’ve set up a simple Dockerized Python web app with a basic CI/CD pipeline file (e.g., for GitHub Actions). The pipeline just builds and pushes the container. Your mission is to secure it. We expect this should take you about 2-3 hours."
The Tasks:
- Integrate a Static Application Security Testing (SAST) tool to scan the code.
- Add a step to scan the final Docker image for known vulnerabilities.
- Implement a secret-scanning check to prevent credentials from being committed.
- Write a short summary explaining your tool choices, trade-offs, and what you’d do next.
This challenge directly measures the core function of a DevSecOps role: embedding security into the development lifecycle. It’s a far better signal of on-the-job performance than asking trivia questions. For more on this, our guide on creating a solid candidate vetting engine provides a complete framework.
Deep Dive: Sourcing and Assessment Trade-Offs
The "post and pray" method of recruitment is a surefire way to fail. The best candidates are passive; they aren't scrolling job listings. Your sourcing strategy must focus on genuine engagement over mass outreach.
Alt text: A hiring manager sourcing security talent by networking in online communities.
This is a necessity in a market with a critical cybersecurity talent gap projected to hit 3.5 million unfilled positions.
Go Where the Talent Lives
Top-tier security professionals are skeptical of generic recruiter messages. Meet them on their home turf.
- Niche Online Communities: Engage thoughtfully in places like Reddit's
r/netsecor specialized Discord servers. Participate, don't just post jobs. - Professional Conferences: Events like Black Hat or DEF CON are for building relationships, not just collecting resumes.
- Open-Source Contributions: Platforms like GitHub are a goldmine. Look for contributors to security tools like Metasploit, OSSEC, or Wireshark. Their code is their resume.
Crafting Outreach That Gets a Reply
Personalization is non-negotiable. Your message must prove you see the candidate as an expert.
"Your recent talk on supply chain security at BSides was insightful. We're tackling a similar challenge as we scale our CI/CD pipeline, and your expertise is exactly what we need. Are you open to a brief chat about the technical problems we're trying to solve?"
This works because it is specific, problem-focused, and respectful. Platforms offering AI-powered recruiting and sourcing can help scale this personal touch.
Choosing the Right Assessment Method
The assessment format is as important as the content. Align the method with the role's core functions.
A blend is often best. A short take-home project followed by a live discussion provides a comprehensive picture while respecting everyone's time.
Checklist: Your Information Security Recruitment Playbook
Use this checklist to audit your process and close gaps before they cost you a great candidate.
Phase 1: Define the Role & Job Description
- Define the Business Need: Pinpoint the specific business risk or compliance driver this role solves (e.g., pass SOC 2 audit, protect PII in new feature).
- Build a Skills Matrix: Separate "must-have" skills from "nice-to-have" skills to widen your talent pool.
- Write an Outcome-Driven Job Description: Frame the role around the mission and impact, not just a list of tasks.
- Sell the Culture: Highlight your dedicated training budget, research time, or blameless post-mortem culture.
Phase 2: Source & Assess Talent
- Go Where Talent Is: Proactively engage in niche communities (Reddit, Discord) and at security conferences.
- Personalize Your Outreach: Reference a candidate's specific talk, open-source project, or blog post.
- Design a Realistic Assessment: Use a practical, hands-on challenge that mirrors a real-world problem and takes 2-4 hours max.
- Use a Consistent Scoring Rubric: Evaluate all assessments with a simple rubric to reduce bias and keep the process fair.
Phase 3: Close the Deal & Onboard for Success
- Craft a Competitive Offer: Benchmark salary and equity, but also emphasize non-monetary perks like training and work-life balance.
- Create a 90-Day Onboarding Plan: Provide a clear roadmap for immersion, contribution, and impact.
- Show a Clear Career Path: Demonstrate opportunities for growth to attract ambitious candidates.
Alt text: A new security hire being onboarded successfully by their team.
The competition is fierce; there are not enough skilled people to fill the open roles. To learn more, you can explore more on the complexities of the cybersecurity skills gap.
What to Do Next
- Audit Your Current Process: Use this checklist to do an honest review of your existing information security recruitment workflow. Where are the weak spots?
- Define Your #1 Priority Role: Get stakeholders to agree on the single most critical security role you need to fill. Focus all your energy there first.
- Scope a Pilot Program: We connect companies with pre-vetted, remote security experts who can start delivering value in weeks.
Start a Pilot
References & Further Reading
- ISACA, "State of Cybersecurity 2025" Report.
- Cybersecurity Ventures, "Cybersecurity Jobs Report."
- ThirstySprout, "AI-Powered Recruiting and Sourcing."
- ThirstySprout, "Candidate Vetting Engine."
Hire from the Top 1% Talent Network
Ready to accelerate your hiring or scale your company with our top-tier technical talent? Let's chat.

